Domains & SSL
Every site and environment on Magelify gets assigned a unique subdomain under *.appcluster.com upon creation. This allows you to access the site immediately without pointing a domain of your own. You can add your own custom domain and remove the default domain from the web UI. Every site comes with free, automatically managed SSL certificates for secure HTTPS protection.
Adding a custom domain
In order to access your site through your own domain, Magelify creates a routing rule which maps the domain name to the NGINX component (web frontend) of your application/site. If you have more than one environment, you can choose which environment to forward traffic to.
To add a new domain follow these steps:
-
From the Site Dashboard > Overview tab, click on the + icon under Domains.
-
The Add new domain dialog appears:
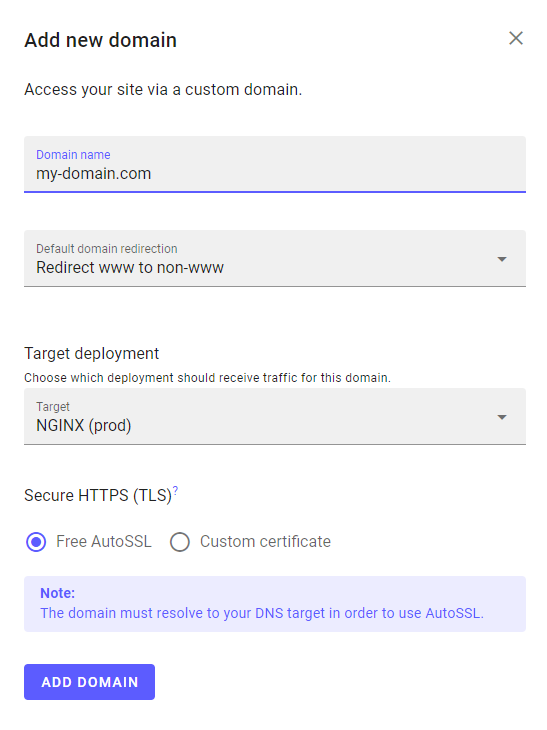
-
Fill out the following information:
- Domain name: the domain or subdomain to forward traffic for
- Default domain redirection: choose whether to redirect all traffic to the www/non-www version of the domain
- Target deployment: choose the environment this domain should be mapped to
- Secure HTTPS (TLS): use a free certificate managed by Magelify* or upload your own
*Your domain's DNS records must be correctly set up in order for AutoSSL to work
-
Click on DNS Settings to obtain the information you need to point your domain to Magelify. We recommend using a
CNAMErecord when possible.
Free SSL/TLS certificates
Magelify offers free and automatically managed TLS certificates powered by Let's Encrypt. We are strong advocates of a more secure web and encourages everyone to use HTTPS. You may easily switch between Let's Encrypt and a custom TLS certificate by editing the ingress rule.
Internal service discovery
Most services on Magelify are closed off from public access. By default only NGINX is accessible externally, which is the service responsible for processing incoming HTTP/HTTPS web requests.
Other services, such as databases are not exposed outside the cluster. This is done to reduce the potential attack surface following the security principle of least privilege. We also have network policies in place which prevents a container from accessing a container/service in another site.
Within the cluster you may still access your service instances through their internal hostname/endpoint. You can find the connection details of a particular service instance from the Addons section in the Dashboard.